| Table of Contents | ||||
|---|---|---|---|---|
|
...
any operation adding, updating, deleting or retrieving metadata for a specific participant that can be identified by the participant id (pid) is performed by the participant that is the owner of that metadata. The metadata owner is in posession of a participant id (pid) and is responsible for the publication and correctness of metadata for that specific PID.
that when a participant makes a request for metadata, it is guaranteed that it is the Administrative Body that has created the response containing that metadata.
The metadata keys therefore consists of two different key pairs. A client key pair used when the participants adds, uppdates, deletes or fetches (get) metadata and a server key pair used for signing and evaluating the response from the Administrative body.
Specific details on how to create and validate Proof of Posession (PoP) tokens in metadata requests using the metadata key pairs are described in MTS5.
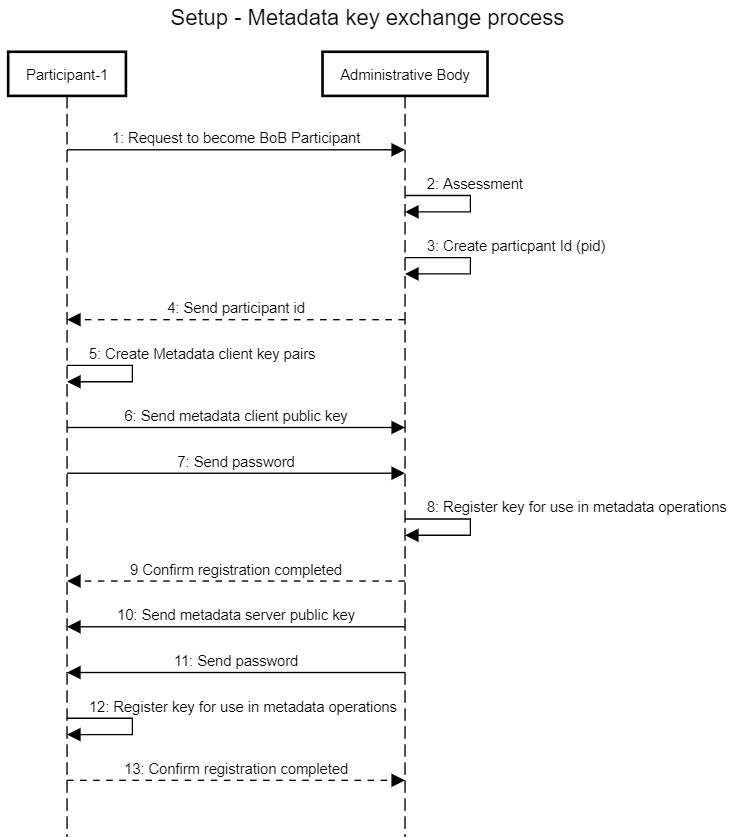
Setup - Metadata keys exchange
An mandatory initial setup is performed for each participant in order make sure that the two main objectives described above for securing metadata is achieved. The setup process involves exchange of both server- and client key pairs and is described in the diagram below. The keys are ECDSA or RSA private/public key pairs. The format used for key exchange is JWK.
...
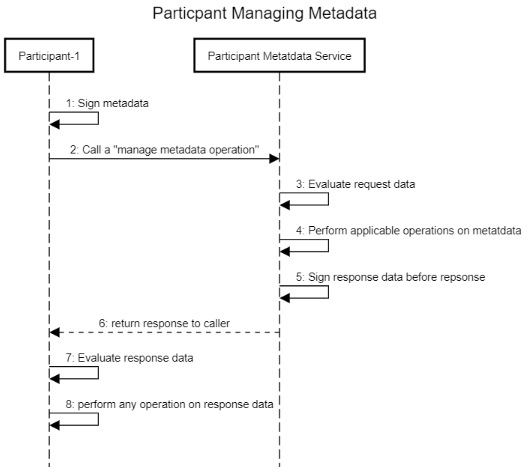
Mechanism - Use of metadata keys
...
The security mechanism for managing participant metadata works as follows.
...
This works equally well when a participant wants to retrieve specific metadata.
...